Singapore, January 16, 2024 — Group-IB, a leading creator of cybersecurity technologies to investigate, prevent, and fight digital crime, has today released a new blog post about one of the most notable pieces of malware of the past year: Inferno Drainer. The research, produced by Group-IB’s High-Tech Crime Investigation unit, details the sophisticated scam-as-a-service scheme, which leveraged high-quality phishing pages to lure unsuspecting users into connecting their cryptocurrency wallets with the attackers’ infrastructure that spoofed Web3 protocols to trick victims into authorizing transactions. Inferno Drainer was active from November 2022 until an announced shutdown in November 2023. Group-IB informed all companies that were affected by the malware to take all necessary steps to mitigate the risks.
Group-IB investigators leveraged the company’s sector-leading Threat Intelligence product to upwards of 100 cryptocurrency brands that were impersonated on phishing pages hosted on more than 16,000 unique domains during Inferno Drainer’s lifespan. In line with Group-IB’s zero-tolerance policy to cybercrime, notifications were issued to brands whose name and likeness were appropriated by the scammers. According to Scam Sniffer, Inferno Drainer has been linked to the theft of more than USD $80 million in digital assets, making it the most prominent crypto drainer of 2023.
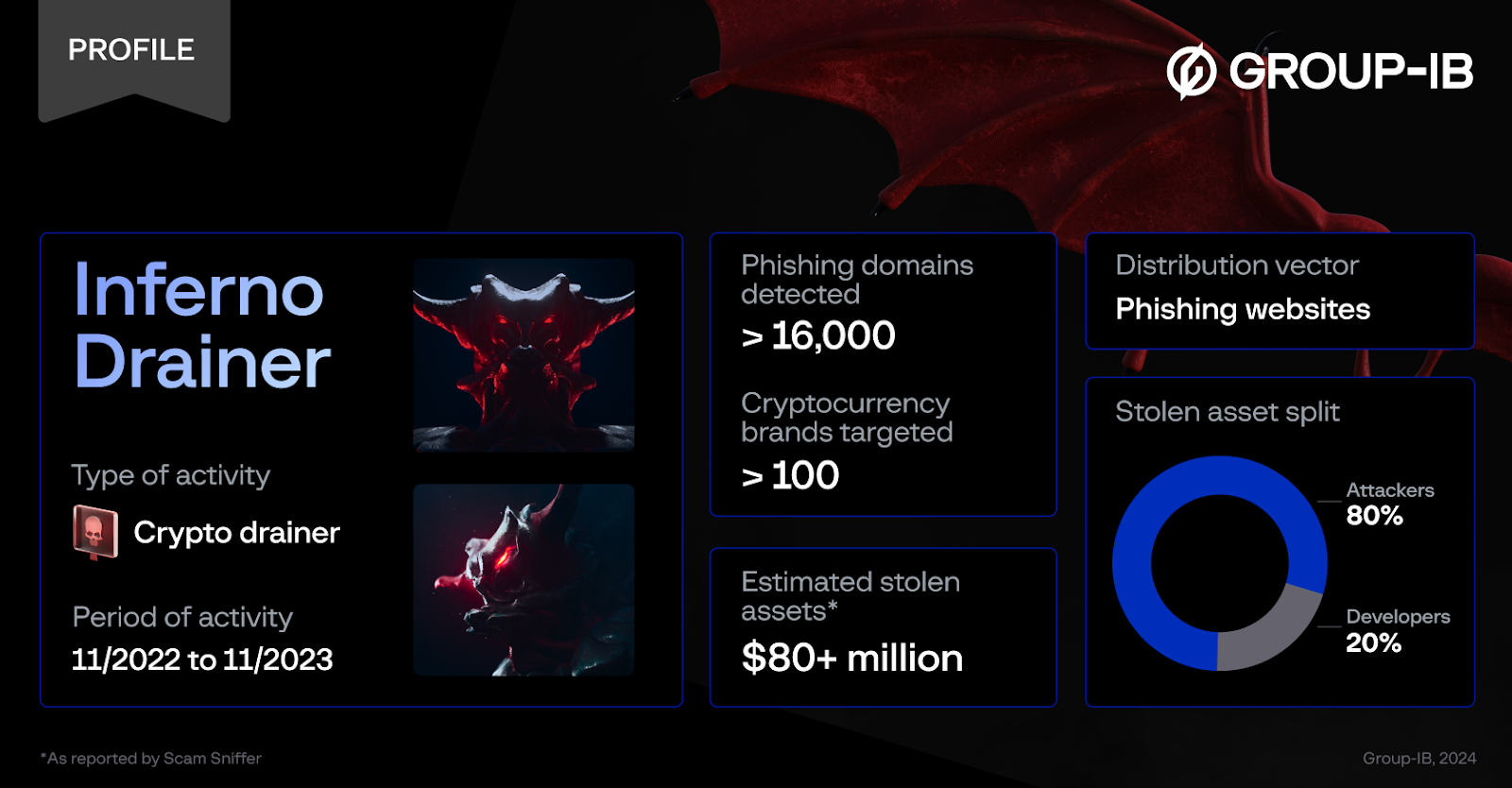
Figure 1. Inferno Drainer profile
Тhe eye of the fire
Inferno Drainer, full name Inferno Multichain Drainer, was a type of malware offered for hire to other cybercriminals under the Scam-as-a-Service model and designed to steal the digital assets of victims fooled into connecting their cryptocurrency wallets and authorizing transactions. The drainer’s developers promoted their malware on a Telegram channel, the first post on which was published on November 5, 2022. Cybercriminals leveraging Inferno Drainer had access to a customer panel, which was still live as of the first week of December, that allowed them to customize features of the malware and detailed key statistics such as the number of victims that had connected their wallets on a specific phishing website, the number of confirmed transactions, and the value of the stolen assets.
Group-IB investigators discovered that Inferno Drainer’s developers charged a flat rate of 20% of stolen assets for use of the drainer, with the users receiving the additional 80%. Cybercriminals wishing to leverage Inferno Drainer could either upload the malware to their own phishing sites, or make use of the developer’s service for creating and hosting phishing websites. In some cases, this service was provided for free; in other cases, the administrators demanded 30% of the stolen assets, Group-IB experts found.
Figure 2. Screenshot of Inferno Drainer’s user panel dated from the first week of December 2023
The phishing pages created by Inferno Drainer, which were promoted on social media sites such as X (formerly Twitter) and Discord, attempted to attract victims with the offer of free tokens (known as airdrops), the opportunity for the victim to mint their NFTs and claim the rewards, or receive compensation for outages caused by cybercriminal activity. The victim is prompted to connect their wallets on this website, initializing the next stage of the scam scheme.
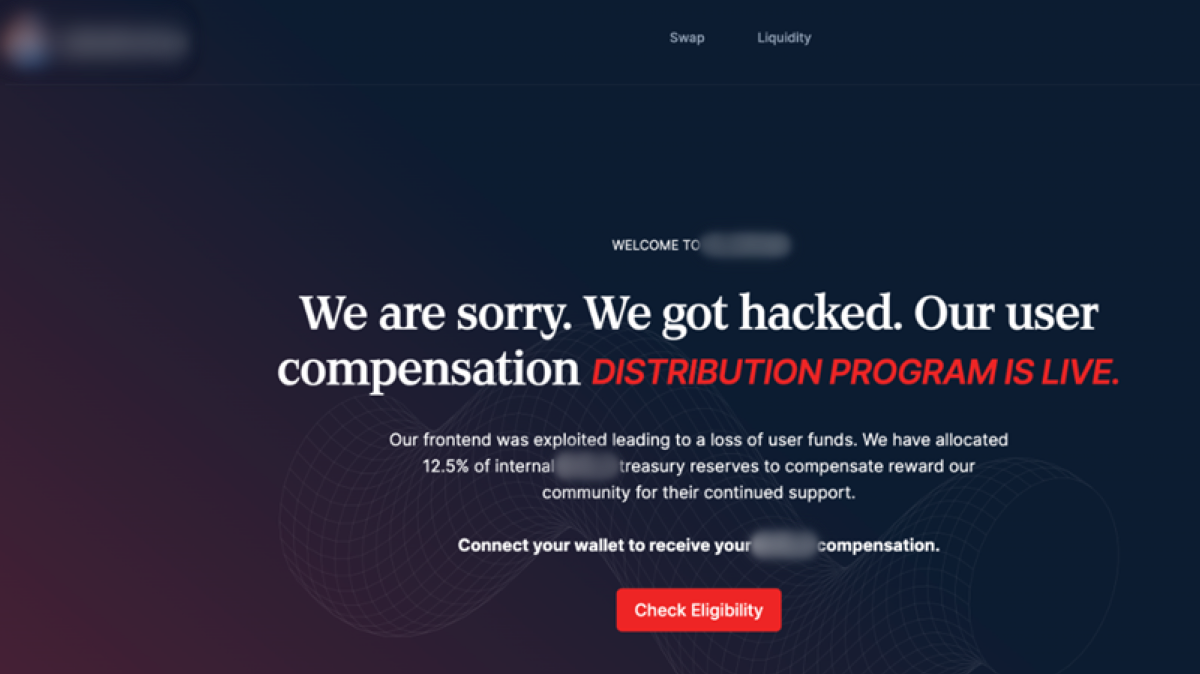
Figure 3. Example of phishing page that contained Inferno Drainer malware.
Inferno Drainer also spoofed popular Web3 protocols designed for the safe and efficient trading of digital assets by allowing self-custody crypto wallets to connect to decentralized applications (DApps). This was done through the use of malicious JavaScript code that masquerades as popular Web3 protocols such as Seaport, WalletConnect, and Coinbase and is embedded on phishing websites to initiate a malicious transaction. Some phishing websites contained multiple scripts impersonating different Web3 protocols. These scripts were accessible to scammers via GitHub repositories or as a separate ZIP file hosted on a file sharing site.
“Inferno Drainer may have ceased its activity, but its prominence throughout 2023 highlights the severe risks to cryptocurrency holders as drainers continue to develop further. The ever-growing sophistication of phishing attacks are leaving increasing numbers of people vulnerable to falling victim, and we urge cryptocurrency holders to remain vigilant and be wary of any website promoting free digital assets or airdrops,” Andrey Kolmakov, Head of Group-IB’s High-Tech Crime Investigation Department, said.
Group-IB recommends that digital asset holders make sure they trust only legitimate websites, such as those contained on CoinMarketCap, to conduct any transactions. The company also urges victims of cryptocurrency crime to save the phishing URL address, save any data related to malicious transactions, and share these with local law enforcement agencies with the aim of bringing evildoers to justice.
About Group-IB
Founded in 2003 and headquartered in Singapore, Group-IB is a leading creator of cybersecurity technologies to investigate, prevent, and fight digital crime. Combating cybercrime is in the company’s DNA, shaping its technological capabilities to defend businesses, citizens, and support law enforcement operations.
In November 2023, Group-IB celebrated the 20th anniversary of its founding with a range of exciting events marking the company’s global growth and significant contribution to international law-enforcement efforts aimed at stamping out cybercrime.
Group-IB’s Digital Crime Resistance Centers (DCRCs) are located in the Middle East, Europe, Asia-Pacific, and Central Asia to help critically analyze and promptly mitigate regional and country-specific threats. These mission-critical units help Group-IB strengthen its contribution to global cybercrime prevention and continually expand its threat-hunting capabilities.
Group-IB’s decentralized and autonomous operational structure helps it offer tailored, comprehensive support services with a high level of expertise. We map and mitigate adversaries' tactics in each region, delivering customized cybersecurity solutions tailored to risk profiles and requirements of various industries, including retail, healthcare, gaming, financial services, manufacturing, critical services, and more.
The company’s global security leaders work in synergy with some of the industry’s most advanced technologies to offer detection and response capabilities that eliminate cyber disruptions agilely.
Group-IB's Unified Risk Platform (URP) underpins its conviction to build a secure and trusted cyber environment by utilizing intelligence-driven technology and agile expertise that completely detects and defends against all nuances of digital crime. The platform proactively protects organizations’ critical infrastructure from sophisticated attacks while continuously analyzing potentially dangerous behavior all over their network.
The comprehensive suite includes the world’s most trusted Threat Intelligence, The most complete Fraud Protection, AI-powered Digital Risk Protection, Multi-layered protection with Managed Extended Detection and Response (XDR), All-infrastructure Business Email Protection, and External Attack Surface Management.
Furthermore, Group-IB's full-cycle incident response and investigation capabilities have consistently elevated industry standards. This includes the 70,000+ hours of cybersecurity incident response completed by our sector-leading DFIR Laboratory, more than 1,400 successful investigations completed by the High-Tech Crime Investigations Department, and round-the-clock efforts of CERT-GIB.
Its solutions and services have time and again been revered by leading advisory and analyst agencies such as Aite Novarica, Forrester, Frost & Sullivan, KuppingerCole Analysts AG, and more.
Being an active partner in global investigations, Group-IB collaborates with international law enforcement organizations such as INTERPOL and EUROPOL to create a safer cyberspace. Group-IB is also a member of the Europol European Cybercrime Centre’s (EC3) Advisory Group on Internet Security, which was created to foster closer cooperation between Europol and its leading non-law enforcement partners.

